Command Line information and FAQ coming soon (should be done by today; May 10, 2009)
This section will incorporate the following information
- Command Line Key Creation
- Command Line Key Server Syncing
- FAQ
Command Line Key Creation
First you will need to use the key that creates your key
This will run the key generating wizard as I call it. The next step is to select what type of kind of key you will like. The choices are DSA & Elgamal, DSA and RSA. If you want it to do encryption then you need to choose DSA & Elgamal.
Code:
Please select what kind of key you want:
(1) DSA and Elgamal (default)
(2) DSA (sign only)
(5) RSA (sign only)
Next it will ask you for the keysize. The default is 2048. I choose to be 4096. The more bits the harder it will be to crack your key.
Code:
DSA keypair will have 1024 bits.
ELG-E keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) 4096
Requested keysize is 4096 bits
Next it will request you say how long the key will be good for. The default value for this is 0. This indicates it will never expire. You can specify <n>w, <m>m <n> y. w= weeks; m=months and y=years. It will then request you to confirm it all.
Code:
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 0
Key does not expire at all
Is this correct? (y/N)
If this is all right then type in 'Y' and hit enter. If not type in 'N' and hit enter.
It will then request you to enter a user id to identify the key. It will go through and ask you to enter several pieces of information. The first one is your full name, then your email address and finally a comment. You can see below what I entered for mine.
Code:
You need a user ID to identify your key; the software constructs the user ID
from the Real Name, Comment and Email Address in this form:
"Heinrich Heine (Der Dichter) <heinrichh@duesseldorf.de>"
Real name: Michael Brown - Test
Email address: michaelbrown2009@gmail.com
Comment: PGP Command Line Test
You selected this USER-ID:
"Michael Brown - Test (PGP Command Line Test) <michaelbrown2009@gmail.com>"
It will ask if you want to change the name, comment, email or if it is okay or quit. If everything is correct type in o. If you want to change the name type in n, for the comment, type in C, for the e-mail address type in E.
It will then request you enter a passphrase. It will give you one dialog box. This box will be for you to enter your passphrase. It will open another dialog box requesting you to enter your passphrase again.
It will then state that it needs to a lot of bytes. This is what it looks after all the bits are done.
Code:
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
+++++.++++++++++.+++++++++++++++.+++++.+++++++++++++++++++++++++++++++++++.+++++++++++++++..++++++++++++++++++++.++++++++++..+++++++++++++++>+++++.+++++>+++++............<+++++....+++++
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
..+++++++++++++++.+++++++++++++++...++++++++++++++++++++++++++++++.......+++++...+++++.+++++.+++++.++++++++++++++++++++....++++++++++.++++++++++++++++++++.++++++++++..+++++..+++++...++++++++++.+++++>+++++.+++++..++++++++++..+++++++++++++++.+++++.+++++.+++++>+++++>.+++++>+++++......>..+++++<+++++..........................................>+++++<+++++....>+++++......................................................................................................>+++++<..+++++..........<......+++++.....+++++^^^^
It will give you the key ID and say it has been marked ultimately trusted
Code:
gpg: key F863DEC9 marked as ultimately trusted
public and secret key created and signed.
It will then give you some information.
Code:
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 3 signed: 3 trust: 0-, 0q, 0n, 0m, 0f, 3u
gpg: depth: 1 valid: 3 signed: 5 trust: 1-, 0q, 0n, 2m, 0f, 0u
gpg: next trustdb check due at 2009-10-20
pub 1024D/F863DEC9 2009-05-10
Key fingerprint = 81A9 A67D 0BB7 3463 D20F A1F2 C581 F033 F863 DEC9
uid Michael Brown - Test (PGP Command Line Test) <michaelbrown2009@gmail.com>
sub 4096g/3791A346 2009-05-10
That is how you create a key via the command line.
Creating Revocation Key/Certificate
You should create a revocation Key or Certificate. This is a good idea because this will/can be use to revoke your public key in case your public key gets compromised.
The command that you need to run is the following
Code:
gpg --output revoke.asc --gen-revoke <KEY-ID>
It will ask you to create a revocaetion certificate for the key that you choose.
Code:
Create a revocation certificate for this key? (y/N)
It will ask you to specify a reason
Code:
Please select the reason for the revocation:
0 = No reason specified
1 = Key has been compromised
2 = Key is superseded
3 = Key is no longer used
Q = Cancel
(Probably you want to select 1 here)
Your decision?
It will then ask you to add a description
Code:
Enter an optional description; end it with an empty line:
It will then ask you to confirm what you have entered
Code:
Reason for revocation: No reason specified
in case my private key becomes compromised
Is this okay? (y/N)
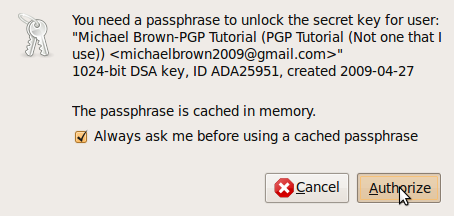
It will then ask you to enter the passphrase that you used for that key to unlock the private key
Code:
You need a passphrase to unlock the secret key for
user: "Michael Brown <bromic94@pct.edu>"
1024-bit DSA key, ID 120867BB, created 2009-03-22
After you enter it it will state the following:
Code:
You need a passphrase to unlock the secret key for
user: "Michael Brown <bromic94@pct.edu>"
1024-bit DSA key, ID 120867BB, created 2009-03-22
You have created your revocation certificate
To use you revocation certification use the following command
Code:
gpg --export -a D8FC66D2 > mykey.asc
Where D8FC66D2 is the Key ID
If you want to use your revocation certificate you need to import your revocation cert and public key in your keyring. The revocation cert will be merged with your public key. You then have to upload your key to the keyservers again. It then will be revoked.
Keep your revocation certificate in a secure location. I carry mine on a USB drive that is under lock and key.
Command Line Key Server Syncing
To upload your public key to the Ubuntu Key server run the following command
Code:
gpg --send-keys --keyserver keyserver.ubuntu.com <KEY-ID>
Where <KEY-ID> is your key Id.
FAQ
What does uploading my key to the keyserver allow me to do?
Uploading your key to a keyserver allows you to communicate with others via a signed or encrypted state. Someone can search for you. If you know you will be communicating with them make sure to give them the fingerprint of the key. This will make sure they get the right one. Years ago I had some issues with PGP key thus I have several out there and I have 1 out there for this tutorial.
Is there another way via a web interface that I can upload my key to the Ubuntu Key server?
You can go to http://keyserver.ubuntu.com:11371/ and scroll down to the Submit a Key section. You will have to get the "ASCII-armored version" of your public key. You can export your public key to your computer, open it, copy the contents and then paste it in the text box on that page.
If there are any questions please let me know and I will add them.












 Adv Reply
Adv Reply




























Bookmarks